Server Security
- Basic server security with safe password
- Overview of Brute Force Attack
- Settings of fail2ban and sshd
* Here is the highlight of YouTube tutorial.
Remote server can let you develop more functional iOS apps but the maintenance
is one of the toughest works we have to be careful about. Remote servers
are always threatened by web service crackers.
The simplest way to try but the hardest way to protect would be Brute Force
Attack. If you set your password with 6 digits of numbers, your system
would be cracked within a few hours without any protection.
So, let's study server security with me with some of my cases I encountered.
Usual linux server can be accessed with sshd and you can confirm the access
log with the following code.
cat /var/log/secure
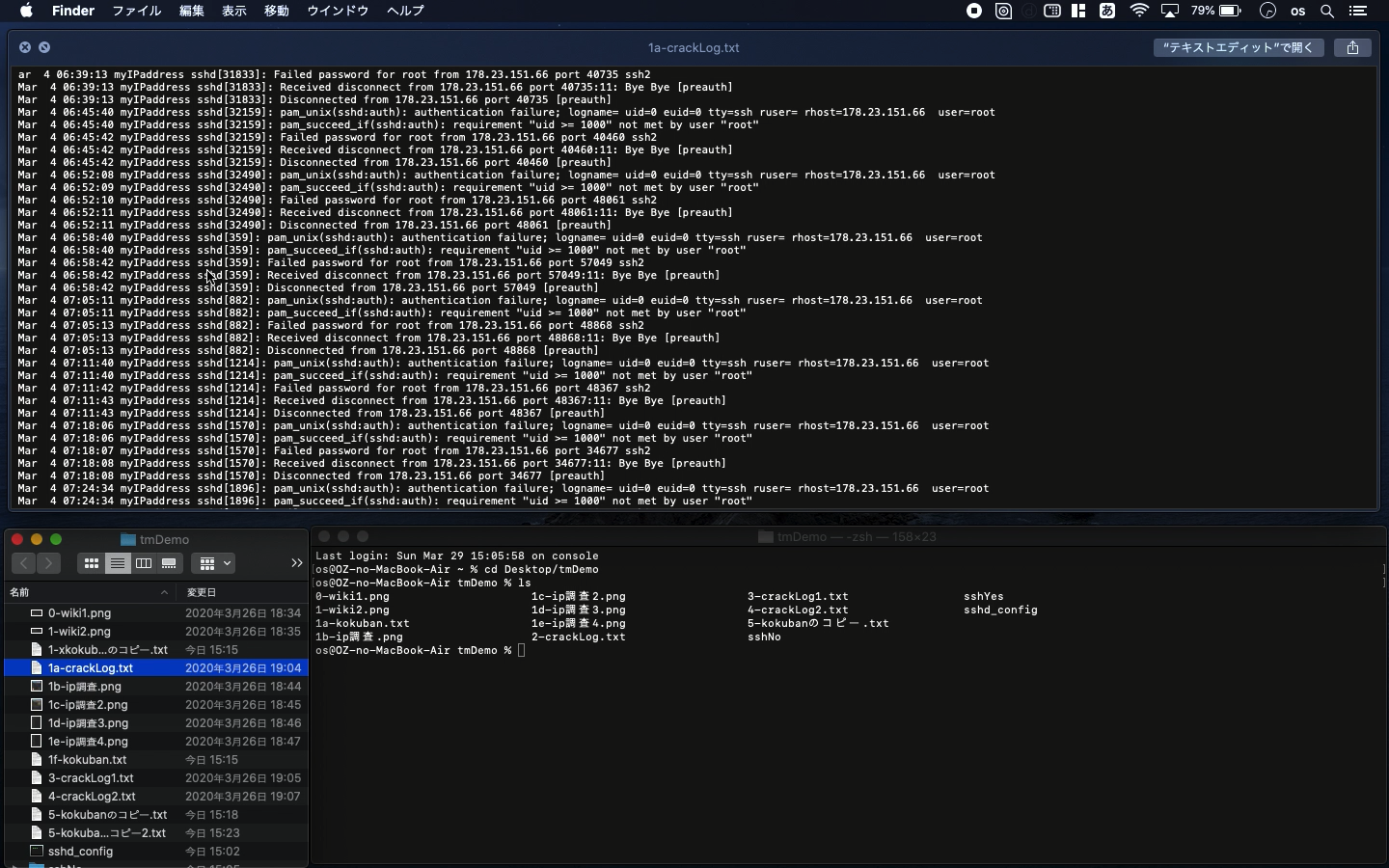
Mar 4 06:39:13 myIPaddress sshd[31833]: Received disconnect from 178.23.151.66
port 40735:11: Bye Bye [preauth]
Mar 4 06:39:13 myIPaddress sshd[31833]: Disconnected from 178.23.151.66
port 40735 [preauth]
Mar 4 06:45:40 myIPaddress sshd[32159]: pam_unix(sshd:auth): authentication
failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=178.23.151.66 user=root
Mar 4 06:45:40 myIPaddress sshd[32159]: pam_succeed_if(sshd:auth): requirement
"uid >= 1000" not met by user "root"
Mar 4 06:45:42 myIPaddress sshd[32159]: Failed password for root from 178.23.151.66
port 40460 ssh2
Mar 4 06:45:42 myIPaddress sshd[32159]: Received disconnect from 178.23.151.66
port 40460:11: Bye Bye [preauth]
Mar 4 06:45:42 myIPaddress sshd[32159]: Disconnected from 178.23.151.66
port 40460 [preauth]
The crackers tried to steal my root password. The history of access record
would be like this. One of the common ways to block the access is that
you should not use the common port number such as "22". This
cracker used the same so you can also prevent this kind of attack with
fail2ban.
IP address: 178.23.151.66
The settings and response of fail2ban are like this.
[root@myIPaddress directory]# fail2ban-client status sshd
Status for the jail: sshd
|- Filter
| |- Currently failed: 10
| |- Total failed: 3562
| `- Journal matches: _SYSTEMD_UNIT=sshd.service + _COMM=sshd
`- Actions
|- Currently banned: 0
|- Total banned: 10
`- Banned IP list: 178.23.151.66
[root@myIPaddress directory]#
In this way, the fail2ban successfuly banned the IP address: 178.23.151.66.
The cracker cannot access my server anymore. To do so, you have to configure
the following setting file.
jail.local
[ssh-iptables]
enabled =
ports =
filter =
logpath =
maxretry =
In this part, maxretry is the number of how many times you can accept the
mistype of password. It will block particular IP address with this settings.
But there was the case fail2ban could not work. Here is another example.
Let me show your the access record below.
Mar 26 18:17:36 myIPaddress sshd[27771]: Received disconnect from 35.199.73.100
port 33200:11: Bye Bye [preauth]
Mar 26 18:17:36 myIPaddress sshd[27771]: Disconnected from 35.199.73.100
port 33200 [preauth]
Mar 26 18:18:19 myIPaddress sshd[27785]: Invalid user winfrey from 15.165.73.38
port 49864
Mar 26 18:18:19 myIPaddress sshd[27785]: input_userauth_request: invalid
user winfrey [preauth]
Mar 26 18:18:19 myIPaddress sshd[27785]: Received disconnect from 15.165.73.38
port 49864:11: Bye Bye [preauth]
Mar 26 18:18:19 myIPaddress sshd[27785]: Disconnected from 15.165.73.38
port 49864 [preauth]
Mar 26 18:18:47 myIPaddress sshd[27800]: Invalid user the from 171.220.243.179
port 53966
Mar 26 18:18:47 myIPaddress sshd[27800]: input_userauth_request: invalid
user the [preauth]
To get the source code, check the comment of my YouTube
Back to Table List

